A security professional deals with so many things to safeguard their company or firm from different kinds of attacks. Memory Forensics is also one of them that helps information security professionals to find malicious elements better known as volatile data in a computer’s memory dump. Now, before jumping to Memory Forensics tools, let’s try to understand what volatile data means and what remains in the memory dump of a computer.
Contents
What is Volatile Data?
When the computer is running, all the clipboard content, browsing data, chat messages, etc remain stored in its temporary memory. These data are called volatile data, which is immediately lost when the computer shuts down. Suppose, you are working on a Powerpoint presentation and forget to save it on your hard drive or any non-volatile storage. Then, you would lose all the work if your computer lost power before saving the document.
What Remains in the Memory Dump?
Memory Dump contains memory data snapshots captured by your computer at a specific instance of time. It’s also known as Core Dump or System Dump. It also contains useful forensics data such as the system’s state before a system crash or security compromise incident. Memory dumps contain various RAM data that can clarify the cause and other key details about such incidents.
Best Memory Forensics Tools For Data Analysis
Memory Forensics provides complete details of executed commands or processes, insights into runtime system activity, information about open network connections, and lots more. Let’s have a look at some best Memory Forensics tools available out there.
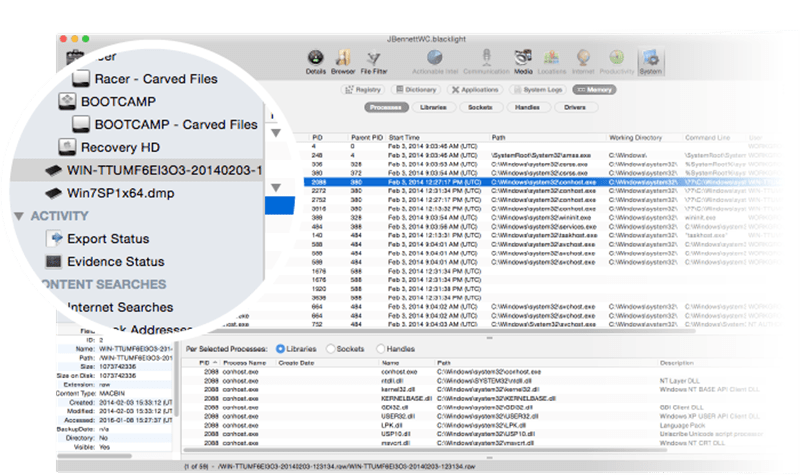
1. BlackLight
BlackLight is one of the best and smart Memory Forensics tools out there. It makes analyzing computer volumes and mobile devices super easy. Apart from that, BlackLight also provides details of user actions and reports of memory image analysis.
It efficiently organizes different memory locations to find traces of potentially important user activities. Blacklight analyzes several types of memory files including hibernation files, and pagefile.sys, raw dumps, and crash dumps. It can also perform bulk extraction content searches for various items such as phone numbers, addresses, URLs, etc.
Blacklight comes with a powerful file filter view and it’s way faster than other open-source forensics tools. You can use this tool to analyze data from all four major platforms i.e Android, Windows, iOS, and MacOS X. BlackLight comes with a hefty price tag but you can request a free trial, use it for some time and then decide whether your team or company need it or not.
Also Read: Four Tips for Improving Your Security Incident Response
2. Volatility
Volatility is another forensics tool that you can use without spending a single penny. Yes, it’s free and helps security professionals understand the power of analyzing the runtime state of a system using the data found in volatile memory (RAM) dumps.
It’s a cross-platform, modular, and extensible platform that allows you to extract useful information about network connections, open sockets, running processes, process DLLs process, cached registry hives, and much more.
This forensics tool is now supported by one of the largest communities and can in many ways in your digital investigation. Volatility is available for Windows, MacOS X, and Linux operating systems.
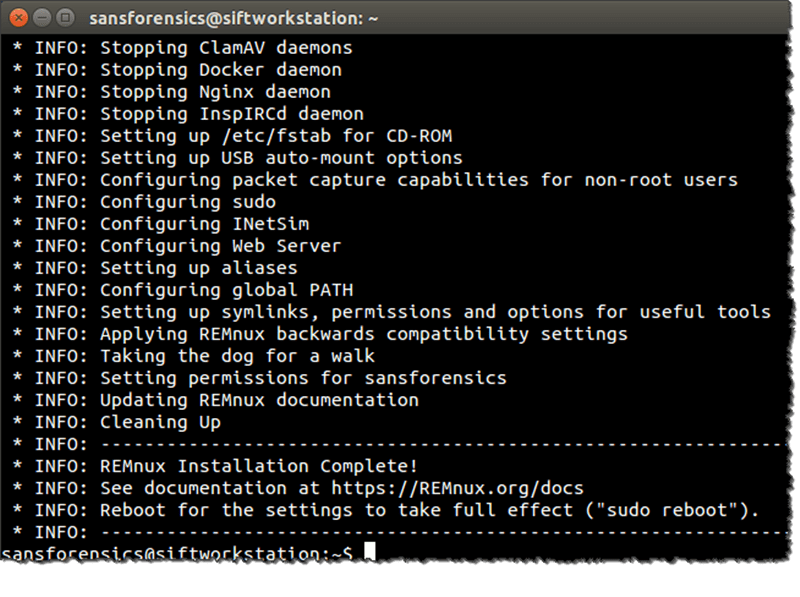
3. SANS SIFT
The SANS Investigative Forensic Toolkit (SIFT) is a popular digital forensics tool that comes with all the essential features. It’s an open-source tool and is known for performing in-depth forensic or incident response investigations.
It supports Advanced Forensic Format (AFF), RAW (dd) evidence formats, and Expert Witness Format for deep analysis. The SANS SIFT comes with a user-friendly interface. You can either launch the required tools from the top menu bar or go with the traditional way of using the terminal window.
It also includes other useful tools such as Rifiuti for examining the recycle bin, log2timeline for generating system logs-based timelines,s and Scalpel for data file carving. SANS SIFT offers better memory utilization, the latest forensic techniques, Auto-DFIR package update, and cross-compatibility between Linux and Windows.
Also Read: Four Best Data Security Tips for Your Business
Final Words
I hope you found the article useful and now understand Memory forensics quite well. There are various digital forensics tools available out there but most of them are either not regularly updated or lack community support. If you own a Ubuntu system, I suggest you go for SANS SIFT. Volatility is good for all of three platforms and lastly, BlackLight is good for big companies and organizations.