In this digital age, finding love online has become increasingly common. Unfortunately, cybercriminals have also evolved their tactics, leveraging the power of artificial intelligence (AI) to execute sophisticated romance scams. AI-powered romance scams are a growing concern as criminals harness the capabilities of AI to manipulate and deceive unsuspecting individuals.
In this article, we’ll explore five ways cybercriminals use AI in romance scams. By understanding these tactics, you can better protect yourself in the realm of online romance. Let’s dive in and uncover the dark side of AI-powered romance scams.
Contents
How cybercriminals exploit AI in romance scams
Here are some ways, cybercriminals make use of artificial intelligence to con people looking for love.
1. AI-Enhanced Profile Fabrication
Cybercriminals utilize AI to create realistic and compelling online profiles, ensuring they appear genuine and attractive to potential victims. AI algorithms can generate convincing profile pictures, craft engaging bios, and even simulate human-like conversation patterns. By employing AI in this manner, scammers can establish trust and emotional connections with their targets, setting the stage for their deceitful intentions.
To protect yourself, exercise caution when interacting with individuals online. Be wary of profiles that seem too perfect or display inconsistencies. If something feels off, conduct a reverse image search to verify the authenticity of the profile picture.
2. Chatbots for Conversation and Emotional Manipulation
AI-powered chatbots enable scammers to engage in prolonged and personalized conversations with multiple victims simultaneously. These chatbots are programmed to simulate human responses, emotions, and even flirtatious behavior. By leveraging AI, scammers can manipulate emotions, build rapport, and exploit vulnerabilities to gain the trust and affection of their targets.
To avoid falling victim to AI-enhanced chatbots, be mindful of suspicious patterns in conversations. If the responses seem generic, lack personalization, or exhibit odd behavior, consider it a red flag. Take the time to verify the authenticity of the person you’re communicating with before becoming emotionally invested.
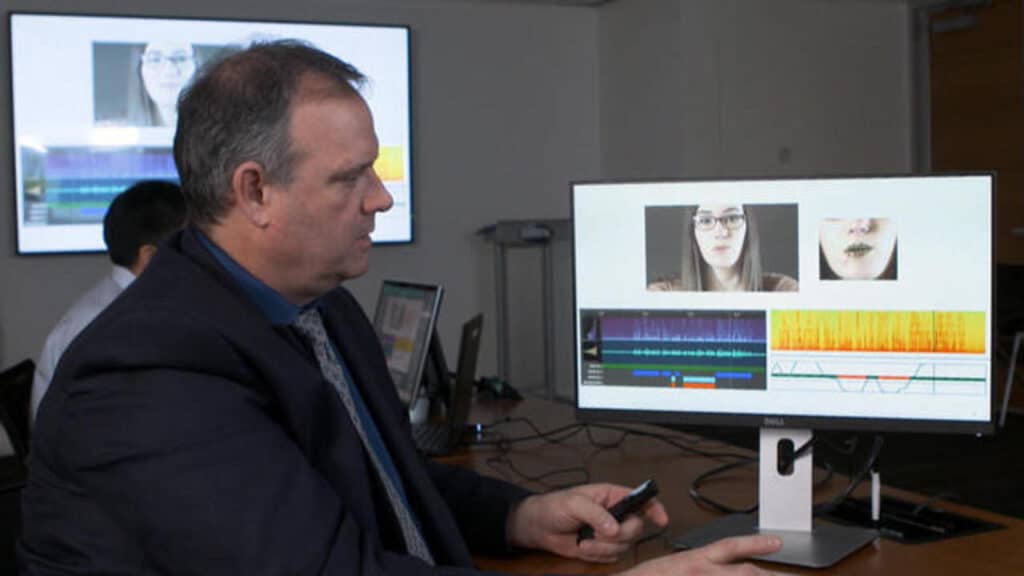
3. Deepfake Technology for Video Calls
Deepfake technology, driven by AI, allows scammers to create realistic video footage by superimposing the faces of unsuspecting individuals onto pre-recorded videos. By employing deepfakes in romance scams, cybercriminals can appear as someone else during video calls, further enhancing the illusion of a genuine connection.
To protect yourself from deepfake-based romance scams, exercise caution when engaging in video calls with individuals you’ve met online. Look for inconsistencies, unusual movements, or visual abnormalities that may indicate a manipulated video. If in doubt, consider using alternative video communication platforms that provide additional security measures.
4. AI-Driven Social Engineering
AI algorithms can analyze vast amounts of data from social media platforms to gather personal information about potential victims. Armed with this information, cybercriminals can craft targeted messages that exploit specific interests, hobbies, or life experiences. By using AI for social engineering, scammers can create a sense of familiarity and trust, increasing the likelihood of successful manipulation.
To protect yourself from AI-driven social engineering, limit the personal information you share on public platforms. Be cautious when receiving unsolicited messages that seem too personalized or refer to specific details about your life. Verify the identity of the person reaching out before disclosing sensitive information or engaging in financial transactions.
5. Automated Scamming Techniques
AI enables cybercriminals to automate various stages of the scamming process. From initial contact and conversation to money requests and follow-ups, scammers can deploy AI-powered systems to handle multiple victims simultaneously. This automation allows them to scale their operations, maximizing their chances of success.
To avoid falling victim to automated AI-powered scams, trust your instincts and be skeptical of anyone requesting money or financial assistance. Be vigilant about protecting your personal and financial information, and never share sensitive details with someone you’ve only met online.
Conclusion
AI-powered romance scams represent a growing threat in the digital landscape. By understanding how cybercriminals use AI in romance scams, you can arm yourself with knowledge and stay vigilant while navigating the world of online relationships.
Remember to exercise caution, verify the authenticity of online profiles, and prioritize your personal safety when interacting with potential romantic partners on the internet. By staying informed and maintaining a skeptical mindset, you can protect yourself from the deceptive tactics of AI-powered romance scams.