Digital rights management (DRM) is a technology used by game developers to protect their software from piracy. Piracy is a significant concern for game developers, as it not only results in a loss of revenue but also negatively impacts their ability to continue developing games. DRM is one of the ways game developers combat piracy. In this article, we will explore how DRM works and its effectiveness in stopping video game piracy.
What is DRM & How Does It Work?
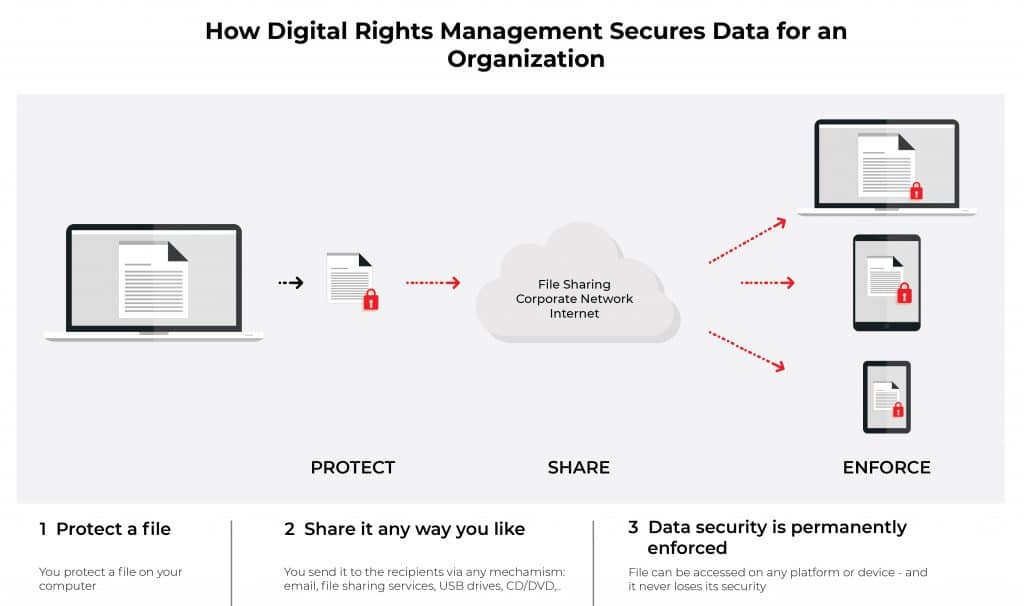
DRM is a technology that game developers use to prevent unauthorized access to their software. The purpose of DRM is to ensure that only legitimate owners of the game can access the software. DRM typically works by encrypting the game code, making it difficult for pirates to copy and distribute the game. How Does DRM Work? DRM works by implementing various methods to protect the game from unauthorized access. One of the most common methods is the use of activation keys. When a game is purchased, the user is given an activation key that they must enter to activate the game. The activation key is unique and linked to the user’s account. This ensures that only the user who purchased the game can activate and play it.
Another method used by DRM is digital signatures. Digital signatures are used to ensure that the game code has not been modified in any way. If the code has been altered, the digital signature will not match, and the game will not run. This prevents pirates from altering the game code to bypass DRM protection. DRM also includes anti-tamper technology. This technology is used to prevent pirates from modifying the game code to remove DRM protection. Anti-tamper technology is designed to detect any unauthorized modifications to the game code and prevent the game from running if modifications are detected.
Effectiveness of DRM in Stopping Piracy
While DRM has been effective in preventing some forms of video game piracy, it has not completely stopped piracy. Pirates have found ways to bypass DRM protection, and there are even online communities dedicated to cracking DRM protection. However, DRM has been successful in reducing piracy and protecting game sales. The presence of DRM on a game sends a clear message to pirates that the game developer takes piracy seriously and will take action to protect their software. This can discourage some pirates from attempting to crack the game.
Additionally, DRM can help to reduce casual piracy. Casual piracy occurs when someone who has purchased the game shares it with friends or family members who have not. DRM can prevent this type of piracy by limiting the number of activations per game key or by requiring each user to have their own unique activation key.
DRM is an effective way for game developers to protect their software from piracy. While it may not completely stop piracy, it does deter some pirates and protect game sales. By using activation keys, digital signatures, and anti-tamper technology, game developers can make it difficult for pirates to copy and distribute their software. The continued use of DRM by game developers will help to ensure the longevity of the video game industry.