In today’s digital age, security is a top concern for users of computing devices. With the increasing prevalence of cyber threats and attacks, it has become imperative for operating systems to provide robust security features to safeguard user data and privacy. Among the various operating systems available in the market, Apple’s macOS stands out for its reputation of being a secure and reliable choice for users who prioritize data protection. In this article, we will delve into the security measures implemented in macOS to understand how Apple fortifies its digital fortress.
macOS is designed with a multi-layered security approach that includes both hardware and software features. These layers work in tandem to provide comprehensive protection against various types of threats, ranging from malware and viruses to social engineering attacks. Let’s take a closer look at the key security features of macOS.
Contents
Secure Boot & Firewall
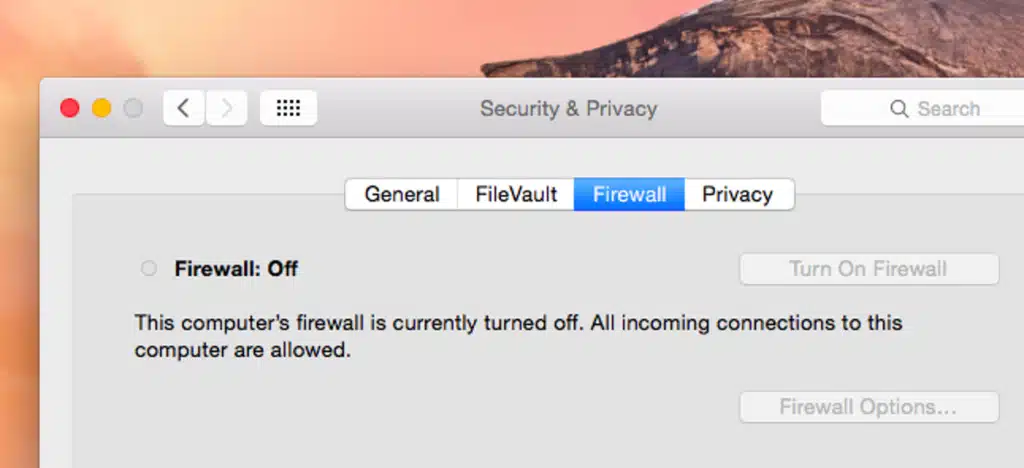
macOS includes a feature called Secure Boot, which ensures that only trusted software is loaded during the startup process. It uses cryptographic checks to verify the integrity of the bootloader, kernel, and other essential components of the operating system. This prevents the loading of unauthorized or malicious software during startup, protecting the system from being compromised at the very early stage of the boot process. macOS comes with a built-in firewall that provides an additional layer of defense against unauthorized network access. The firewall monitors incoming and outgoing network connections and can be configured to allow or block specific connections based on predefined rules. This helps users control which apps and services can communicate over the network, reducing the risk of unauthorized access to their Mac.
macOS also includes a feature that automatically checks for and installs software updates, including security patches, to keep the system up-to-date with the latest fixes and improvements. This ensures that known vulnerabilities are addressed in a timely manner, reducing the risk of exploitation by malicious actors. Users can customize the update settings to suit their preferences, ensuring that their system remains protected with the latest security updates.
Gatekeeper, XProtect, & SIP
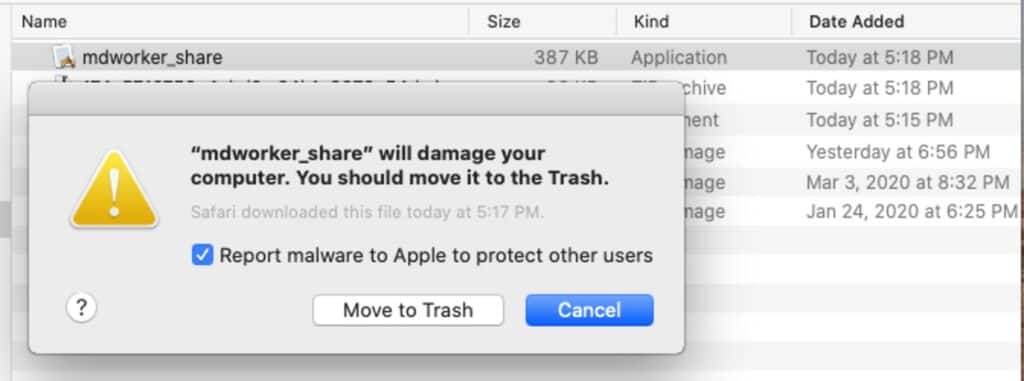
One of the first security features that macOS users encounter is Gatekeeper, which acts as a gatekeeper at the entry point of any software installation. Gatekeeper ensures that only legitimate and trusted software from Apple’s App Store or identified developers can be installed on a Mac. This helps prevent the installation of malicious software, as it verifies the software’s digital signature before allowing it to run. Users can also customize Gatekeeper’s settings to allow software from specific sources, giving them control over what can be installed on their system. macOS includes a built-in antivirus feature called XProtect, which scans files and identifies known malware and viruses. XProtect is constantly updated with new virus definitions, providing real-time protection against known threats. This feature works silently in the background, without any need for user intervention, making it a powerful defense against common malware.
System Integrity Protection (SIP) is a security feature introduced in macOS El Capitan that protects the core system files and directories from being modified or tampered with, even by users with administrative privileges. This prevents malware from gaining unauthorized access to critical system files, safeguarding the integrity of the operating system. Another important feature is Sandboxing is a security feature that isolates apps from each other and from the underlying system, preventing them from accessing sensitive data or performing unauthorized actions. macOS requires apps to be sandboxed, which means they are restricted to their own designated areas and cannot access files or data from other apps without explicit user permission. This containment approach reduces the risk of malware spreading across the system and minimizes the potential damage that can be caused by a compromised app.
Conclusion
In conclusion, Apple’s macOS is equipped with a robust security infrastructure that encompasses both hardware and software features to protect users from various types of threats. From Gatekeeper and XProtect for malware detection, to System Integrity Protection and FileVault for data encryption, to sandboxing and privacy protections for app isolation and user privacy, macOS provides multiple layers of defense against unauthorized access and data breaches. Other security measures, such as Secure Boot, built-in firewall, automatic software updates, and strict guidelines for third-party app developers, further bolster the security of the operating system. User education and transparency initiatives also empower users to take proactive steps in securing their Macs.