Public Wi-Fi is pretty useful. You get to go to a café and get some work done, or maybe kill some time online while waiting at the airport. Public Wi-Fis are a godsend when you’re abroad, giving your all not to use roaming, or to end up with insane fees. However, while they are extremely useful, they are also not that safe. Namely, open public networks are prone to many hacking attacks and attempts. Today, we will be dealing with the so-called Man in the Middle Attacks, as well as ways you can deal with them.
Contents
What is a Man in the Middle Attack?
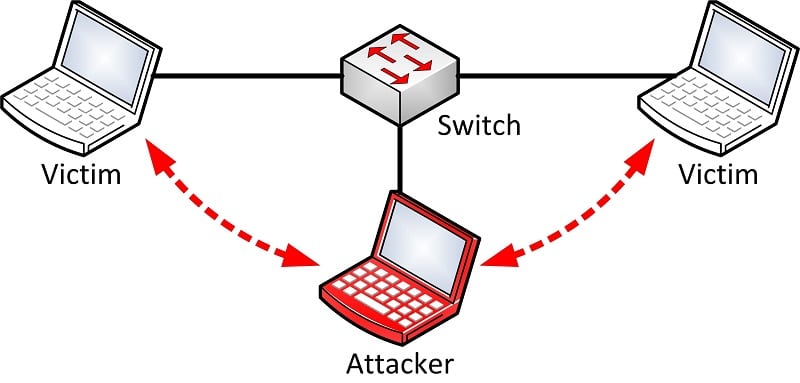
A Man in the Middle Attack (MITMA for short) is basically the hacker intercepting your communication with a router (thus being the man in the middle, between you and the router). The hacker intercepts the information your device sends to a public Wi-Fi network and then uses it for his or her own erosional gain.
Namely, the attack goes through two phases – interception and decryption. Interception is where the traffic of information between your devices and the network gets, well, intercepted. Hackers get a look at all the information you are sending to the device. This can be things like your passwords on your social media, your work email, or even your bank account information. After this, the decryption phase begins. Here the hacker has to actually make sense of the information you sent.
How to protect yourself?
Now, understand what this is half the battle. What matters much more is how you will actually defend yourself. You don’t have to be a tech genius to get this – simply stick to some of the tips below and you will most likely be fine.
Keep an eye on the website you use
First things first – try to keep an eye on the websites you use. Namely, browse only websites that start with HTTPS. When you’re on public Wi-Fi checking out websites that actually start with HTTPS means they are encrypted, which can give you the right amount of extra security so that a hacker will leave you alone.
HTTP websites, on the other hand, aren’t as safe, and we suggest you avoid them. Also, go to trustworthy websites that have protection already. Look out for sites that are safe, that have some kind of sign or label of protection, websites that are secured by an external company.
Better safe than sorry
This is a rather simple one – maybe try not using public networks for anything important. If you’re going to latch onto public Wi-Fi don’t use it for anything more than social media and fun. Avoid accessing your bank account, your work email, your credit card information… Stick to just relaxation and unimportant things.
If you are in a bind and really need to get some work done, try to at least stick to aspects that won’t really be of use to a hacker. For example, don’t access your work email, maybe use your phone’s data for that one. Stick to general information, excel spreadsheets and tips, and stay away from sensitive info.
Get a good VPN
Another thing you could try is getting a solid VPN to hold your back. Namely, VPN (or virtual private network) is there to protect your data and information from anyone who wants to look at it, but shouldn’t. Namely, a VPN encrypts your data, it gives you a different IP address. Imagine your information going through a tunnel, instead of taking the regular route. This tunnel shields your data, it serves as protection against anyone with prying eyes.
Now, VPNs aren’t that difficult to set up and you can even get great service for free. Just check out this thorough listing of free VPNs, choose one that seems ok to you, follow the simple instructions, and you are ready to go. And yes, these are completely legal.
Firewalls and automatic connections
Stick to privacy screens, and avoid automatic settings. Namely, go to your settings on your device, and disable the “connect automatically” feature that it most likely has. The reasoning behind this is that you don’t want your device to connect to whatever Wi-Fi option it finds. Your computer might be hacked, and you might not even notice it unless you know the signs.
You also want to keep an eye out for firewalls and issues of that nature. Namely, a firewall is there to prevent data packets with malicious content to enter your device. It’s a very important line of defense that too many people shut off. Simply go to your safety and security settings, snoop around, and turn it on again. Most smart gadgets and computers give you the option to do so.
Conclusion
Man in the Middle Attacks is a common and nefarious method hackers use to get a hold of your data. These most often happen when you try to access public networks. However, with some common sense, and the right software, you can avoid spreading valuable private information. Get a VPN, be mindful of your privacy settings, and stick to the instructions in this article and you should have no reason to worry.