Data is one of the most valuable parts of information systems. Almost every organisation in this industry are using some sort of database-powered web applications. Structured Query Language or SQL is used to store, retrieve and manipulate data in the database.
Today, I will talk about SQL injection and its types. If you are into database-related jobs or a cybersecurity enthusiast, this article will help you a lot.
Read: 4 Ways to Secure Your Database
Contents
What is SQL Injection?
SQL Injection is used to attack data-driven applications by inserting a large number of malicious SQL statements into the execution field. It’s a code injection technique helps hackers to destroy the database, a vital part of any organization.
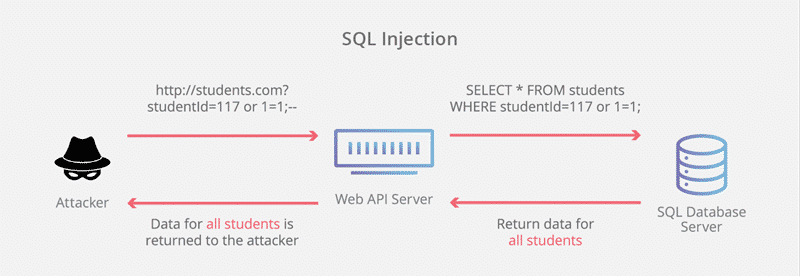
The SQL injection is also a type of hacking known as injection attack or web hacking technique. This attack inserts malicious code into the database by giving input at a web page.
Though these inputs usually have some conditions, they are always true. Hackers can easily pass security tests and get data from SQL database. They can also add, modify and delete records in the database.
The database may be anyone among MySQL, SQL Server, Oracle, SQL Server, etc. SQL injection attacks generally work on dynamic SQL statements. These attacks also have the capability to harm the entire system if it is poorly designed.
If a website or an application is poorly designed then these attacks may harm the entire system. At this point, cybersecurity comes into the picture.
SQL injection attack depends on the database engine and differs from engine to engine. When we asked for input by the system on the webpage like username and password. May be unintentionally but hackers are giving you access to add something directly into the database.
Also Read: Secure your website from SQL injection Vulnerabilities
Types of SQL Injection
Error-based SQL injection
In this type of injection, the hacker analyses different operations and find the error pattern in the database. Then, he/she access it to make their desires fulfilled.
Classic SQL injection
In this technique, the hacker uses the results from the database and hack the database to get things done. It’s also called In-band SQL injection
Union-based SQL injection
This technique is also a part of in-band SQL injection. In this technique, the user combines the query and get the result back as some part HTTP response.
Inferential SQL injection
This is one of the most dangerous types of SQL injection. Here, the hackers do not use the band to get data from the database. They can change the structure of the database by observing patterns of the database. This attack takes longer time and the output is also not visible to Hacker.
Time-based Blind SQL injection
This SQL injection technique is used by hackers to put the payloads. Here, hacker gives time to the database to execute the query. This makes this attack slow in nature.
Out-of-band SQL injection
Out-of-band SQL injection is a not-so-common feature-based attack. It’s generally used in situations where hacker needs to use different channels to attack and get the result. These techniques depend on the database server’s ability to make DNS or HTTP requests to deliver data to the hacker.
Final Words
That’s it for this article. I hope you now understand the basics of SQL injections. Just remember, that creating a database is the most crucial step. If you will follow some standard security practices carefully, the chances of data loss will be reduced to a great extent.

