You might have already freaked out by the title alone. Well, I’m not here to give you a heart attack on what happened but what has happened is in the past. So let me tell you what actually happened.
Contents
Storytime
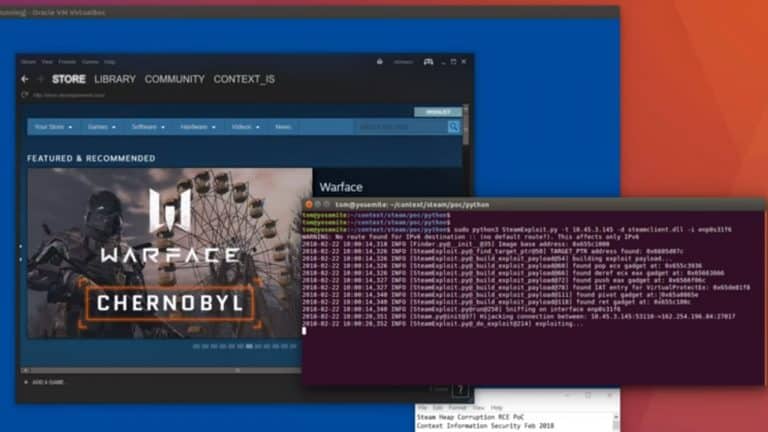
Some time ago there was a bug in steam that nobody noticed. A bug so vulnerable that it that could compromise your security and take over your pc. Security researcher Tom Court has blogged about the bug and its potential misuse, explaining that, “At its core, the vulnerability was a heap corruption within the Steam client library that could be remotely triggered, in an area of code that dealt with fragmented datagram reassembly from multiple received UDP packets.”
Demonstration
The following video demonstrates what could happen if someone tried to exploit that vulnerability in Steam. If the attackers were successful, they could install a software and run it remotely. For test purposes, they ran a calculator app to show how vulnerable Steam users were at that time.
As you can see in the video, the results are quite astonishing. It also throws light on how much damage could have caused if this bug was ever discovered earlier by the wrong people.
What now?
Thanks to Steam’s quick response, the bug was fixed within 8 hrs of its report and a beta patch was rolled over on March 22nd. To us users, it was just one of those Steam’s regular updates complete with fixes to the in-game overlay and problems involving corrupt items on the Steam Workshop, while it also fixed the vulnerability in Steam.
Court also added, “this was a very simple bug, made relatively straightforward to exploit due to a lack of modern exploit protections. The vulnerable code was probably very old, but as it was otherwise in good working order, the developers likely saw no reason to go near it or update their build scripts. The lesson here is that as a developer it is important to periodically include aging code and build systems in your reviews to ensure they conform to modern security standards, even if the actual functionality of the code has remained unchanged.”
Stay tuned for more!!