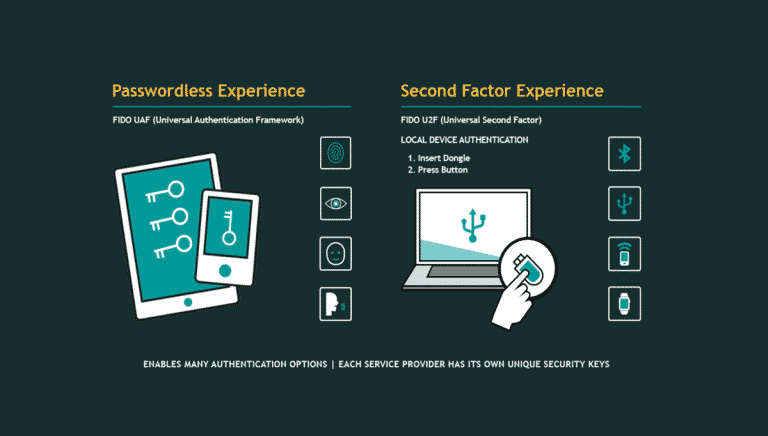
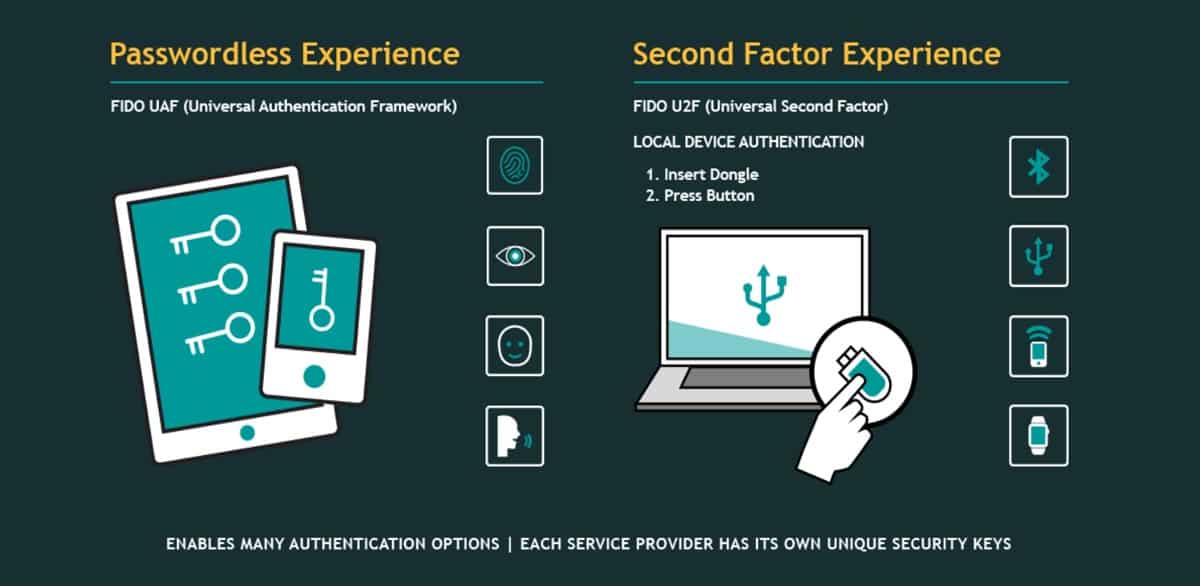
FIDO and W3C have allied with the support of major browsers like Mozilla Firefox, Google Chrome, and Microsoft Edge to resist phishing and provide stronger authentication to protect the data of web users. On 10th April 2018, they have achieved the global milestone of forming the ubiquitous authentication for the web users.
World Wide Web Consortium (W3C) and FIDO Alliance have achieved this milestone of forming the simpler yet stronger way of authenticating the data of the users across the world. The W3C has come up with an advanced Web Authentication (WebAuthn), which is a collaborative effort of the Web API specifications and it was submitted by the FIDO to the W3C, for the Candidate Recommendation (CR) stage.
The CR is a product of the Web Authentication Working Group, which is a team of representatives from more than 30 member organizations. So, CR is a stage which is implemented before the final approval of the web standard. W3C has invited web app developers to implement WebAuthn.
Also Read: Password Secrets: Why Your Password is Never Secure
What is WebAuthn?
WebAuthn is a process to define the standards of a Web API which can be incorporated in the browsers and web platform infrastructures to provide the new methods to securely authenticate the web with the help of browsers and devices.
WebAuthn is developed by W3C with the coordination with FIDO Alliance and it is a primary part of the FIDO 2 project along with the FIDO’s Client to Authenticator Protocol (CTAP) specification. CTAP functions when the external authenticator communicates with the user’s internet device.
External authenticator like a mobile phone has to communicate using strong credentials locally with the user’s internet device. FIDO 2 project enables the users to authenticate the online services with mobile devices or desktop with the enhanced phishing resistant security.
https://youtu.be/5ZIQabDrnT0
Google, Mozilla, and Microsoft have started to support the WebAuthn standard in their browsers and have started implementation for the Windows, Linux, Chrome and Mac platforms. Both the CTAP and WebAuthn specifications are available today which will enable the developers to build the support for the next generation of FIDO authentication into their products.
The implementation of the FIDO 2 efforts, promotion of the WebAuthn and the commitment of the browser vendors to implement the FIDO Authentication protection opens a new era for the internet users.
Online services and enterprises who are looking to protect themselves and their customers which involves the risks related to the passwords which include phishing, stolen credentials, and several attacks can soon start using standard authentication process that will work through browser or external authenticator. So, deploying the FIDO Authenticator can enable the users to choose the users accessing through various devices.
The standards of the FIDO 2 project will reach out across the globe and many companies have taken an oath to start implementing the FIDO authenticator in their browsers and operating system. Simultaneously, FIDO will also launch the certificates to the servers and authenticators who are adhering to the FIDO standards.