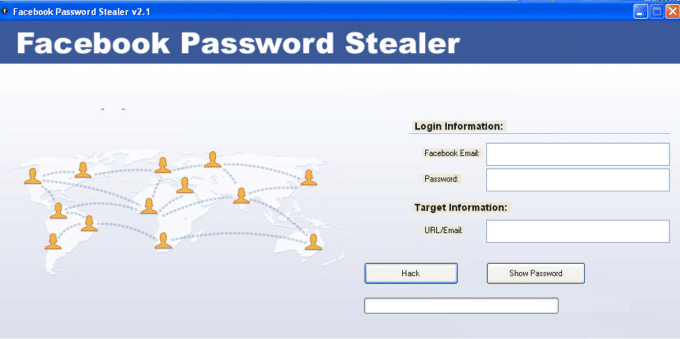
The “Facebook Password Stealer” tool is actually a RAT as it turns out to be.
Almost every newbie hacker has this passion for hacking other people’s Facebook account. While some people actually understand the amount of effort and knowledge required for successfully “hacking” something, most people think there exists a “software” which does the task by clicking on that “hack” button.
Hackers are known to be smart and above all adaptive to changes. A bunch of cybercriminals was able to “sniff” this fantasy and they found a carrier for their malware. The result was a tool claiming to be a Facebook password stealer which claimed to give you the password of any account just by entering account URL or email id used on Facebook.
Have a look at the UI:
You can see there is a catch! you have to enter the credentials of your Facebook account on the first hand. But this is not it, according to a team of security researchers going by twitter handle of @malwarehunterteam, this program actually installs backdoors on your computer which escalate privilege as soon you permit the app to run in administrator mode and then open a reverse connection to its origin. Once infected, these things can be done on your system:
- Remotely gain access into the victim’s desktop or active window
- See the victim’s IP, full computer name, full username, OS, install date, and country
- Remotely execute a file from disk or URL
- Manipulate files
- Open a remote shell, allowing the attacker to use the command line
- Open a process manager to kill processes
- Manipulate the system registry
- Record the computer’s camera and microphone
- Log keystrokes
- Steal passwords stored in browsers or other applications.
Therefore, it is highly advisable to stay away from such tools which claim to “hack” something effortlessly.
This is the original tweet by the @malwarehunterteam.
Image Credits: MalwareHunterTeam.