The more advanced technology becomes, the more we put our information at risk. As the internet of things broadens, household objects become hackable devices. Our credit card information is stored everywhere. Our very identities are vulnerable to attack. Which is why privacy online is becoming incredibly important.
And yet, most of us tend to hope for the best and throw caution to the wind. We use public WiFi connections, we use unsafe websites and download torrents, and share our information with even more applications and devices than before.
If you still have not secured your data, it is past time that you did so. Not only is it important that you’re cautious around public networks, but your own private home network should be protected too.
You must be sure to pick the right type of security since the differences can leave you and your family open to identity theft. We’re going to focus on two types of security measures. VPNs and proxies.
Read: What is a VPN and How does a VPN Work?
Contents
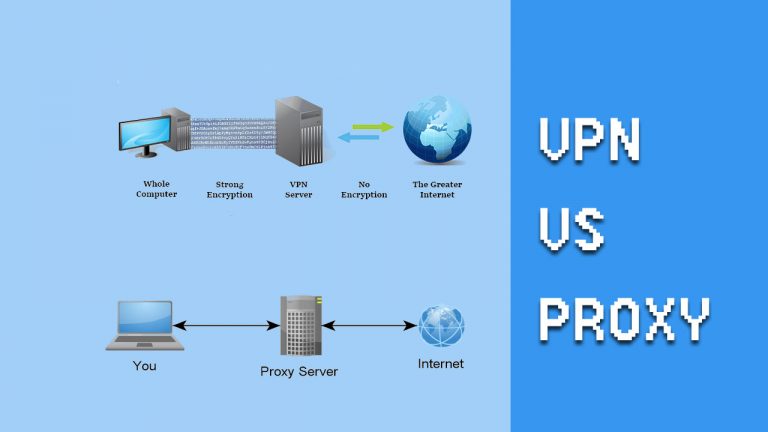
The difference between a proxy and a VPN
A proxy works by redirecting all your traffic through a remote server, making it appear that your connection is coming from somewhere else. So, if you’re in the Middle East, you can make it appear that you’re in the US. Not only does this allow you to unblock websites that may be unavailable in your location, but it also protects your location from being identified by the websites you use.
Proxies are useful for low-risk activities, such as viewing restricted content, and they are relatively cheap. However, they don’t encrypt your data, which leaves you open to hackers and surveillance.
This is why you might consider instead using a VPN. A VPN works by encrypting data used through your browser and operating system. They secure your IP address, location, web information, and applications. Although they route your content through a remote server, just like a proxy, they are far more secure.
Using a proxy
If you do decide to use a proxy, in a private home network when you are not doing anything risky, you have two options: HTTP and SOCKS. HTTP proxies deal with web-based traffic, while a SOCKS proxy includes File Transfer Protocol, which can help you with downloading torrents and the like. Of course, if you are downloading torrents, you should consider using a VPN instead.
While there are free proxies out there, you are far more secure using paid options. Ultimately, you get what you pay for.
Using a VPN
If you need your data to be encrypted, you should use a VPN service. There are some who will argue that everyone should use a VPN, as we are all vulnerable to hackers and government surveillance. Either way, if you’re going to get a VPN, you should do your research and choose a well-reviewed, paid service. Once again, while there are free services out there, they are limited, and ultimately you’re putting yourself at risk.