Lookout, A mobile security firm warned about a new malicious virus ‘NotCompatible malware’ that can harm Android-powered smartphones or tablets and remote them for their dirty work like spamming users, carrying out click-fraud, automated exploitation and fraudulent online ticket purchasing etc.
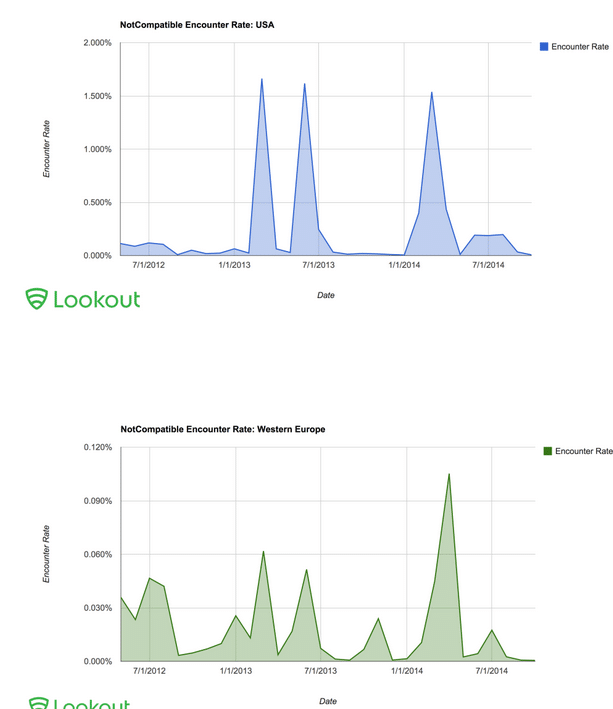
Lookout has confirmed that more than 4 million phones in the U.S. have been turned into botnets this year as a result.
Lookout firm was tracking the evolution of this malware from last past two years. On that time ‘NotCompatible malware’ is used as a proxy to run spam campaigns or scalp concert tickets. After sometime hacker revealed NotCompatible.A, was relatively simplistic architecturally, NotCompatible.C is a changed beast in terms of the technological concepts it uses to stay alive.
How NotCompatible malware spreads ?
NotCompatible malware spreads onto smartphones by infecting a legitimate website and when users visit that website from their phone, they unwittingly download the malicious code.
NotCompatible malware typically introduces itself as an Android system update and asks for permission to install in mobile devices. One way to safeguard against infection is to decline such prompts and go through smartphone settings to check for system updates.
The most common way for the virus to get on a smartphone is by visiting legitimate websites that have been hacked and then booby-trapped to secretly infect visitors, according to Lookout security researcher Jeremy Linden.
This particular strategy is “one of the first times hacked websites were used at a large scale to specifically target and infect mobile devices,” said Tim Strazzere, Lookout’s lead research and response engineer, in a blog post.
Using the NotCompatible proxy, an attacker could potentially do anything from enumerating vulnerable hosts inside the network, to exploiting vulnerabilities and search for exposed data.
You can read more about it on the official blog of lookout by clicking here .