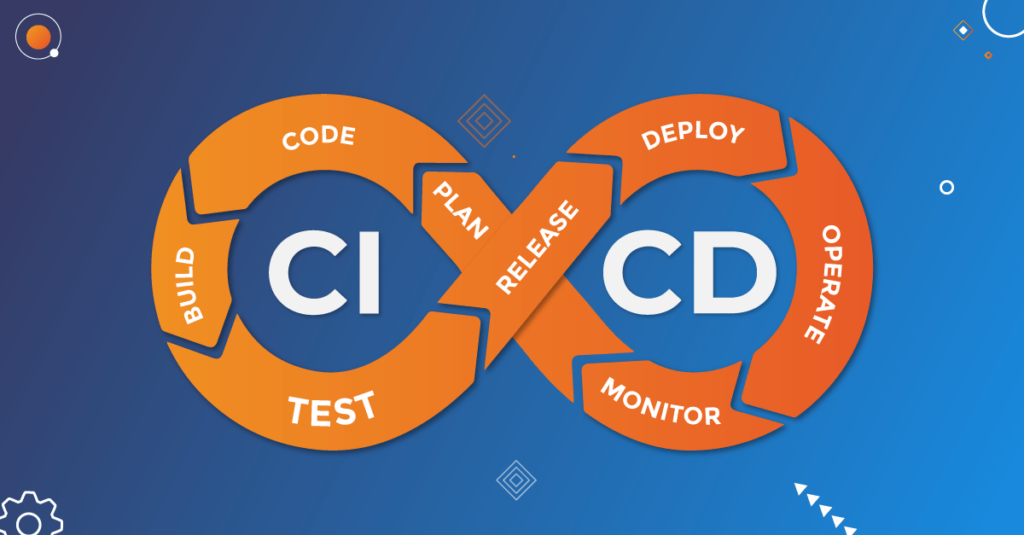
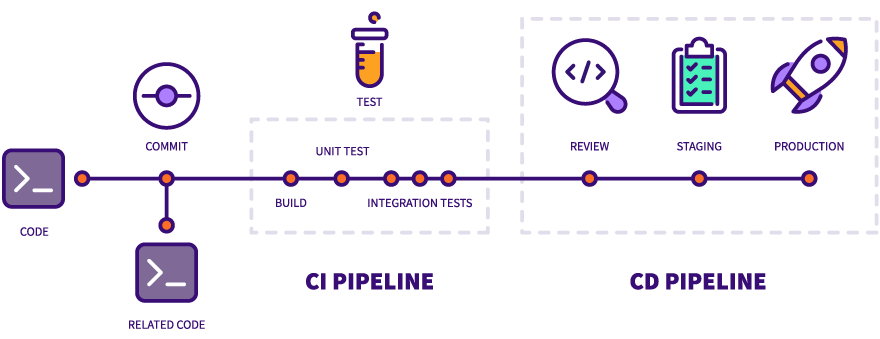
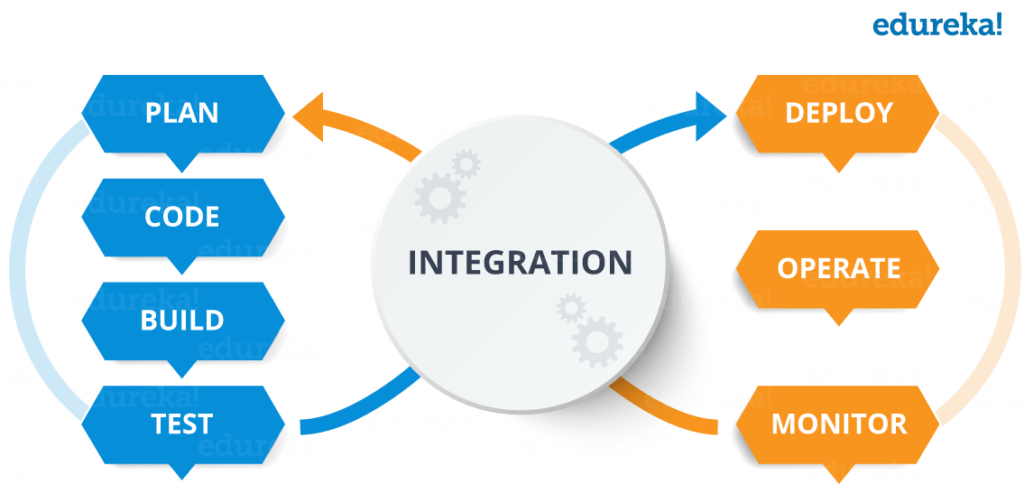
With the fast-paced nature of software development today, security is a major concern for businesses. As the number of security threats and data breaches continues to grow, developers are under pressure to ensure the safety of their applications. One effective way to achieve this is by adding security testing to your continuous integration and continuous deployment (CI/CD) pipeline. This helps to ensure that security measures are in place at every stage of the software development process.
But how do you actually go about automating security testing in your CI/CD pipeline? Well, it’s all about setting up the right tools and processes.
Contents
Step 1: Choose a Security Testing Tool
Choosing a security testing tool is an important first step to automating security testing in your CI/CD pipeline. You need to choose a tool that can scan for various types of security vulnerabilities such as SQL injection, cross-site scripting, and command injection. There are several tools available such as OWASP ZAP, SonarQube, and Gauntlt. Evaluate these tools based on their features, compatibility with your existing CI/CD pipeline, cost, and ease of use.
Step 2: Define Security Testing Scenarios
The next step is to define the security testing scenarios that you want to automate. You can use a combination of tools and manual testing to identify the vulnerabilities in your application. You need to choose the scenarios that are most relevant to your application and cover all possible attack vectors. You can include scenarios like vulnerability scanning, penetration testing, and threat modeling.
Step 3: Integration Into Your CI/CD Pipeline
Once you have chosen the security testing tool and defined the testing scenarios, you need to integrate the tool into your CI/CD pipeline. You need to choose the right stage in the pipeline to include the security testing tool to ensure that it is done at the right time. For example, you can include the security testing tool after the build process or before deploying the application to production.
Step 4: Configure the Security Testing Tool
After integrating the security testing tool, you need to configure it to work with your application. You need to provide the tool with the necessary inputs such as the application URL, authentication details, and testing scenarios. You need to ensure that the configuration is done correctly, and the tool is set up to scan for the vulnerabilities that you have defined.
Step 5: Analyze the Security Testing Results
After the security testing is completed, you need to analyze the results to identify any vulnerabilities that were detected. The security testing tool will provide you with a detailed report on the vulnerabilities that were found. You need to prioritize the vulnerabilities based on their severity and take necessary action to fix them. You also need to ensure that the vulnerabilities are fixed before deploying the application to production.
In conclusion, automating security testing in your CI/CD pipeline is an essential step to ensure the security of your applications. By following these steps, you can integrate security testing into your CI/CD pipeline and automate the process of identifying vulnerabilities. With the right security testing tool and a well-defined testing plan, you can achieve a high level of security for your applications.