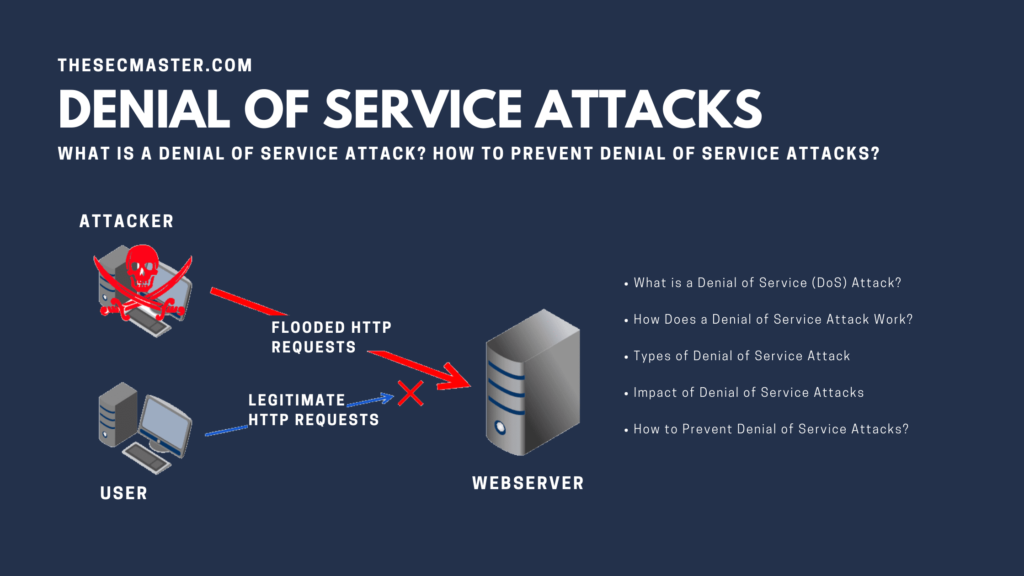
A Denial of Service (DoS) attack is a type of cyber attack where the attacker aims to disrupt the normal functioning of a website, server, or network by overwhelming it with traffic. This attack can be carried out in various ways and can have serious consequences for the targeted organization, ranging from loss of revenue to damage to its reputation.
Contents
Types of DoS Attacks
DoS attacks can take many forms, including flood attacks, application layer attacks, and Distributed Denial of Service (DDoS) attacks. Flood attacks involve sending a massive amount of traffic to a target’s network, which can cause the network to crash or become unavailable. These attacks can take various forms, such as ICMP, UDP, SYN, HTTP, DNS, and NTP.
Application layer attacks, on the other hand, are designed to exploit vulnerabilities in specific applications or services. One example is the Slowloris attack, where the attacker sends a large number of incomplete HTTP requests to a server, causing it to become overloaded and unavailable. HTTP POST attacks, where the attacker sends a large number of HTTP requests with large payloads, are also an example of application layer attacks.
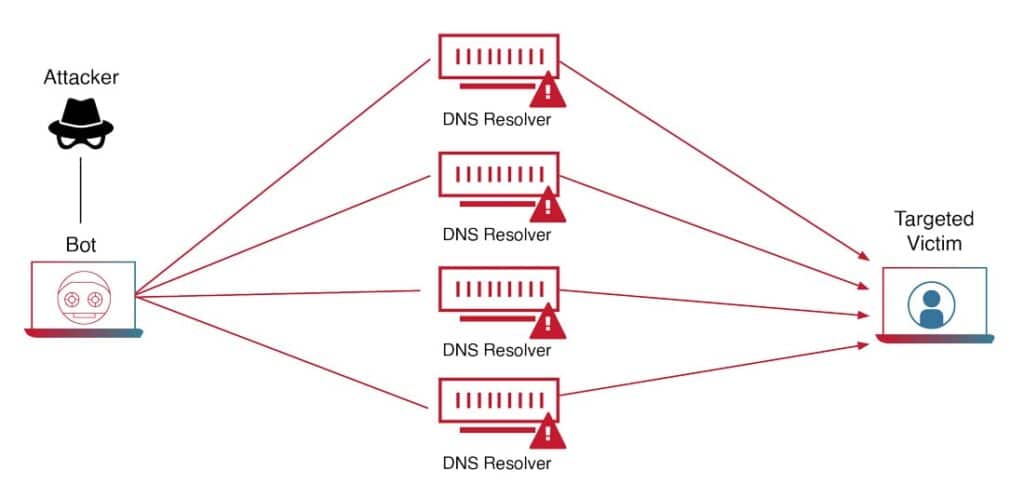
DDoS attacks are a more sophisticated form of DoS attack that uses a network of compromised computers to flood a target’s network or server. This type of attack is often carried out using botnets, which are networks of compromised devices controlled by the attacker. In amplification attacks, the attacker takes advantage of vulnerable servers to amplify the traffic being sent to the target.
How DoS Attacks Work
DoS attacks work by overwhelming the target’s resources, such as bandwidth, processing power, or memory. By flooding the target with traffic or requests, the attacker aims to make it unavailable or unresponsive to legitimate users. In some cases, the attacker may also exploit vulnerabilities in the target’s software or network infrastructure to amplify the impact of the attack.
DDoS attacks are particularly effective because they use a large number of devices to launch the attack, making it harder for the target to block the traffic. These attacks can be carried out using a variety of techniques, including UDP flooding, DNS amplification, and TCP SYN flooding.
The impact of a DoS attack can be severe, ranging from temporary disruption to long-term damage. For example, a DDoS attack can cause a website or service to become unavailable for hours or even days, resulting in lost revenue and damage to the organization’s reputation. In some cases, a DoS attack may also be used as a diversion tactic to distract the target while the attacker carries out other attacks, such as stealing data or installing malware.
How to Prevent and Mitigate DDoS Attacks
One of the most effective ways to prevent DDoS attacks is to invest in DDoS protection services. These services use sophisticated technologies such as deep packet inspection, traffic analysis, and behavior-based detection to identify and mitigate DDoS attacks in real time. By filtering out malicious traffic before it reaches your network, DDoS protection services can ensure that your website and other online resources remain available during an attack.
Another way to prevent DDoS attacks is to optimize your network architecture. By implementing a redundant network infrastructure with multiple internet service providers, you can reduce the impact of DDoS attacks. This strategy can ensure that your network remains available even if one of your ISPs is targeted by an attack.
Traffic filtering and rate limiting are effective strategies for mitigating DDoS attacks. By filtering out traffic from known malicious sources and limiting the amount of traffic that reaches your network, you can reduce the impact of DDoS attacks. These strategies can also help you identify and block traffic that is being generated by compromised devices in your network.
The Takeaway
DoS attacks are a serious threat to organizations of all sizes. These attacks can disrupt online services, compromise sensitive data, and damage an organization’s reputation. By understanding the nature of DDoS attacks and adopting the strategies outlined above, organizations can minimize the impact of DDoS attacks and ensure that their online resources remain available and secure. While it’s impossible to prevent all DDoS attacks, taking proactive measures to prevent and mitigate such attacks can go a long way in protecting your organization from these threats.