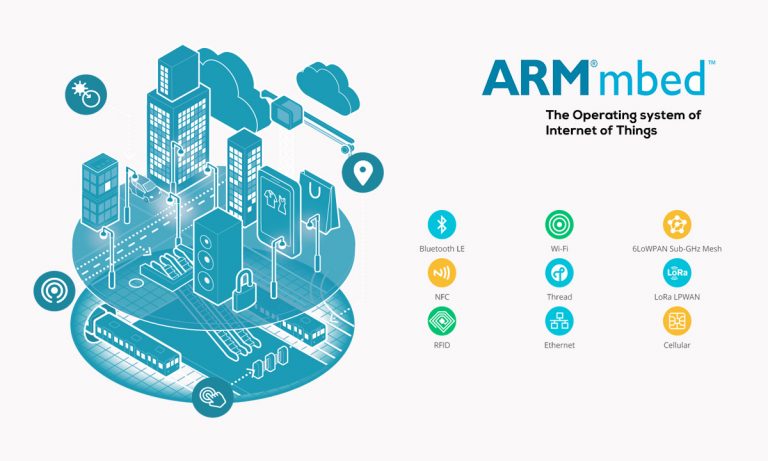
Most programmers are familiar with Windows, Linux, Android and Apple’s iOS. None of them are new, none of them lend themselves to the technology that is going to represent 90% of the lines of code in the next decade. The IoT (Internet of Things) is being led by ARM whose processors are powering in >95% of mobile phones.
The key feature to their success is their exceptionally low energy demands. They have proven themselves time to time. They resisted bloating the silicon with Thumb and Jazelle – both use a lookup table. So, every instruction is actually executed as a 32 bit (and now 64 bit) ARM instruction within the processor. More recently they have added onboard GPUs aimed at the lower end handsets. But as always, low-power has been the chief aim.
All of the lessons learned from the handset (and SIM) designs either by them or by others who have obtained licenses. It gives them the confidence to write an OS for systems that cost cents rather than dollars per unit. They are already part of the team behind the BBC Micro. It is a pico computer with a 16MHz ARM Cortex M0+ with 16 Kbytes of RAM and 256 Kbytes of ROM. Every school child in the UK is given one of these tiny machines in their first year in secondary education.
Contents
The Operating System for Internet of Things
Considering ARM’s history of long-term investment, teaching a generation to learn their new Mbed Operating System which is currently in its 5.5 release IS long-term but is giving notice to the world. This is a new departure for ARM and happily, they have avoided the pitfalls of closed development. I’m sure many readers can attest that being an independent developer normally entitles you to ZERO technical support. Not so with MBed. Free to join the community and a console-like (from my experience) technical support. The people who support you are the people writing the OS!
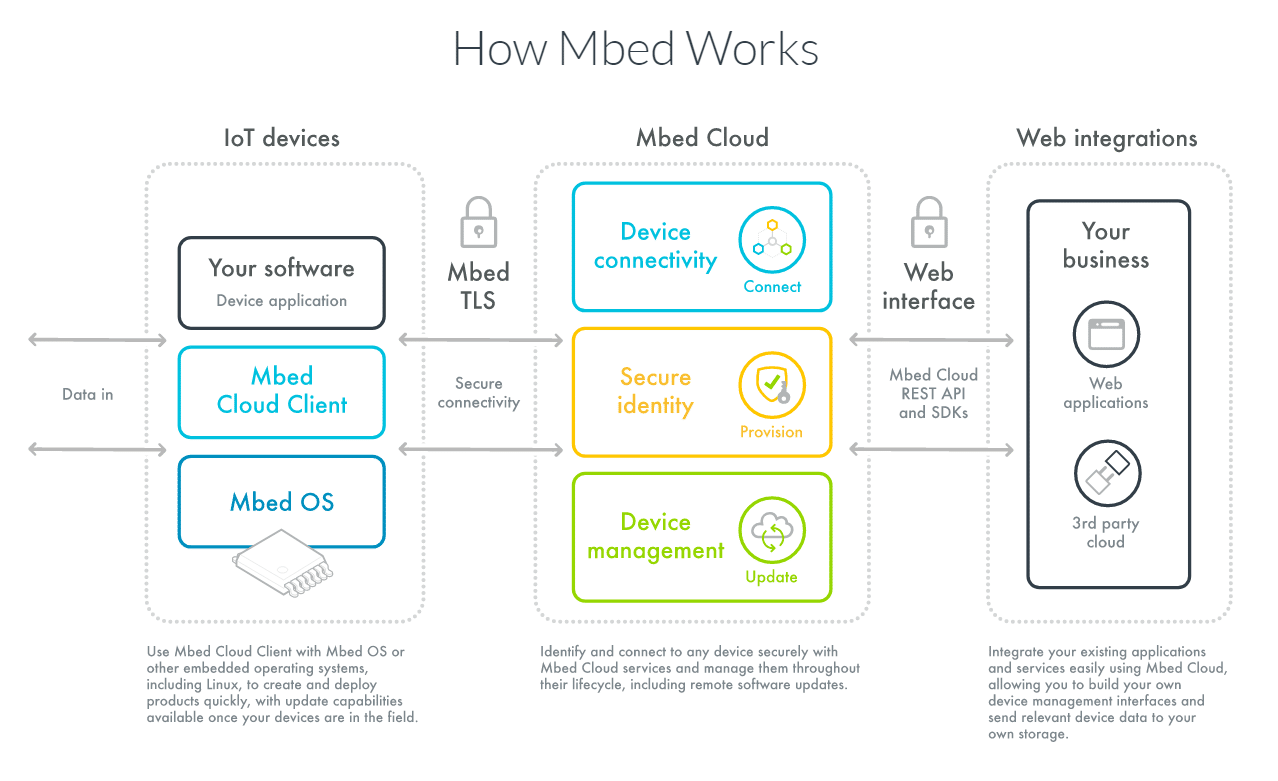
So like every new OS, seeing its development cycles tell us quite a lot about their thinking. At first glance, it reminded me of the Nintendo 64’s OS. Both pre-emptive and program-mediated multitasking and multithreading are available and the CPU ‘sleeps’ when no processing is required. The difference is that it’s the all-important power consumption that is important. Many of the fields describing a process are to manage power. You can even compile code on-line making bug-finding that little bit simpler.
Clearly, C++ is the language it was designed for but Python and other languages are becoming available. Github is where the code is shared and the volume of traffic is increasing rapidly. Certainly there are other IoT Operating System options but as far as I know, it’s the only option that means that your code ends up used by all. I’m developing a speech codec so incorporating code into the OS ensures that everyone can play with the functionality and decide if it becomes a standard.
Here are several examples of practical IoS application:
1) Real-time control of home electronics with feedback.
This covers everything from ‘waking’ your home when you are expected home but able to use your proximity (automatically) via your phone through physical proximity of manual changes via any capable internet service. Now think about heating, lighting, cooking, air-conditioning, washing machine, tumble-drier, and dishwasher… just for a start. Presuming you have Wi-Fi within your home, it will all be free. Your refrigerator will suggest meals from food about to pass its use-by date, your washing machine and dryer will analyze how dry and how soft your clothing is and recommend a conditioner and when your oven needs cleaning, there is sure to be a ‘preferred’ cleaning product. That is the ‘value added’ aspect of the IoT.
2) Stock management, control, and analysis.
While large concerns currently use bar-codes and increasingly QR codes, soon printed silicon will provide every physical object with a unique CPU that draws its power from local Wi-Fi signals. An item can be traced back to the individual workers who made the item to payment and onwards to sales, shrinkage, and support. An item knows when it is being stolen, acts as a receipt to the buyer and item data for items returned due to malfunction all sit on a single system. That is the ‘price value’ aspect of the IoT.
3) Physical, data & currency security.
We are seeing an increase in the pieces of data we require to hold which rely on inherited security. From electronic locks to ID to Bitcoin hashes to paper money. The user is always at the bottom of the security chain. With variegated forms of security, inherent costs rise. The single most common form of unique ID in the world is the SIM card. Anybody who has played with one of these knows that AVR and ARM have almost 100% of the market. There is no surprise that ARM is becoming more and more common. When you know what a SIM can do, it can be annoying that you only have such minimal control of an item that you bought.
Now consider security with each of YOU being at the top of a given chain. You can give someone a key giving them limited access to your car, your office or your home? While a physical key can be copied, we have robust digital security that can be tailored to give someone a subset of your data. Rather than needing an external system to verify a digital transaction, distributed security is less liable to hacking. Payment via digital currency is already seen with loyalty cards in chain stores and by credit/debit cards and a stolen banknote can be traced. While governments like central control, citizens can feel empowered that they control security. This vision has both price-value and ‘perceived value’.
I’ve avoided doing it to a great deal of technical data, those ready to code would do well to read https://docs.mbed.com/docs/mbed-os-handbook/en/latest/ and I will posts some nice snippets of both C++ and assembly-language code because it is my opinion that the ARM core will prevail and if you can provide the customers functionality requirements on a ¢67 chip while other developers need a ¢81 chip, that is a saving of $120000 if 1 million chips are made. This is where the skills and experiences of hackers will pay off. I’m using ‘The Definitive Guide to the ARM Cortex-M0’ book (I still like paper) but Everything in the book is free here https://developer.arm.com/products/processors/cortex-m/cortex-m0-plus