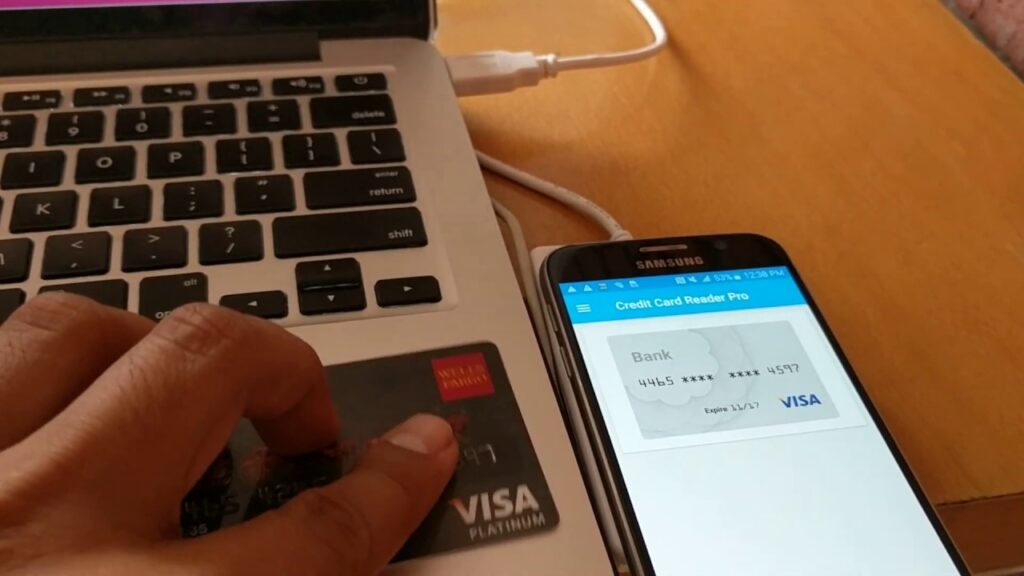
Near Field Communication (NFC) technology has revolutionized the way we interact with our devices, making contactless payments, data transfer, and connectivity effortless. However, as with any technology, NFC comes with its own set of security risks and vulnerabilities.
In this article, we’ll delve into the world of NFC security risks and shed light on the potential threats associated with NFC usage. By being aware of these risks, you can take proactive steps to safeguard your digital world. Want to know about the security threats associated with NFC usage, read on.
Contents
What is NFC Technology?
Before we delve into the security aspects, let’s quickly understand what NFC technology is all about. NFC enables wireless communication between two devices in close proximity, typically within a few centimeters. This technology allows for seamless information exchange, making it ideal for contactless payments, access control, and data transfer.
NFC Security Risks: Protecting Your Digital World
1. NFC Security Vulnerabilities
While NFC technology provides convenience, it is not immune to security vulnerabilities. One of the key concerns is eavesdropping, where an attacker intercepts the communication between two NFC-enabled devices. This can result in the theft of sensitive information, such as credit card details or personal data.
To mitigate this risk, it’s crucial to ensure that your NFC-enabled devices have the latest security patches and updates. Additionally, be cautious when using NFC in public spaces, as attackers may attempt to exploit vulnerabilities in crowded areas.
2. Unauthorized Data Exchange
NFC allows for seamless data transfer, but it also opens the door to unauthorized exchanges. An attacker can use malicious apps or modified NFC tags to manipulate your device and transfer malware or malicious code. This can lead to data breaches, unauthorized access to your personal information, and even financial loss.
To protect against this risk, it’s essential to exercise caution when accepting NFC data transfers from unknown sources. Disable automatic NFC acceptance settings on your device and only accept transfers from trusted sources.
3. NFC Relay Attacks
NFC relay attacks involve intercepting and relaying communication between an NFC-enabled device and another NFC reader. Attackers can use this technique to gain unauthorized access to secure systems, such as door locks or access control systems. This can pose a significant threat in scenarios where NFC is used for physical access control or authentication purposes.
To mitigate the risk of NFC relay attacks, consider using additional security measures such as encryption, authentication protocols, or biometric verification. Implementing multifactor authentication can add an extra layer of security to prevent unauthorized access.
4. Data Leakage and Privacy Concerns
NFC-enabled devices store and transmit sensitive information, including credit card details, personal identification, and contact information. If an attacker gains access to this data, it can result in identity theft, financial fraud, or privacy breaches.
To protect against data leakage and privacy concerns, regularly review your NFC device settings and restrict access permissions to apps or services that require NFC functionality. Additionally, consider using secure NFC payment apps that offer robust encryption and tokenization to protect your financial information.
Conclusion
NFC technology has undoubtedly simplified various aspects of our lives, but it’s crucial to be aware of the associated security risks and vulnerabilities. By understanding NFC security risks, such as NFC security vulnerabilities, and potential threats, you can take proactive measures to protect your digital world.
To enhance NFC security, keep your devices updated, exercise caution when using NFC in public spaces, and be mindful of accepting data transfers from unknown sources. Implement additional security measures like encryption, authentication protocols, and multifactor authentication to safeguard against potential attacks.
Remember, staying secure in the digital age requires a proactive approach. Stay vigilant, educate yourself on NFC security best practices, and enjoy the benefits of NFC technology while keeping your digital world safe from security threats associated with NFC usage.