Windows 10 Devices Could Be Fully Compromised Due To A Huawei Driver
Microsoft is still dependent on various third-party vendors for drivers and other components. There’s nothing wrong in outsourcing but it doesn’t allow the manufacturer to ensure complete integrity of the system.
According to an official blogpost by Defender Research Team, Microsoft has explained the severity of a massive security flaw found in a device management driver developed by Chinese player Huawei.
Table of contents
Huawei’s Device Management Driver was the Culprit
First, the Redmond giant successfully spotted the flaw in Huawei’s MateBook line of laptops. The threat has been identified using the new kernel sensors of Windows 10 version 1809, that is designed to trace user APC code injection initiated by kernel code. The new sensors already helped the company to better investigate the kernel threats like DOUBLEPULSAR.
These sensors were mainly put in place to safeguard the system from NSA-created backdoors like DOUBLEPULSAR. You might be surprised to know that these backdoors were also exploited by WannaCry ransomware.
While we can’t ignore the user APC code injection technique, it’s not that easy to find threats running in the kernel. “Since PatchGuard was introduced, hooking NTOSKRNL is no longer allowed; there’s no documented way drivers could get a notification for any of the above operations. Hence, without proper optics, the only sustainable strategy would be applying memory forensics, which can be complicated,” said the Microsoft Defender team.
The new set of kernel sensors was mainly developed with an aim to deal with these kernel threats. Microsoft Defender ATP uses these sensors to detect suspicious operations invoked by a kernel code and prevent code injection into user-mode. This investigation was also triggered by one of such unusual operations. The alert process tree not only exposed a strange memory allocation but the execution was also happening in the context of services.exe by kernel code.
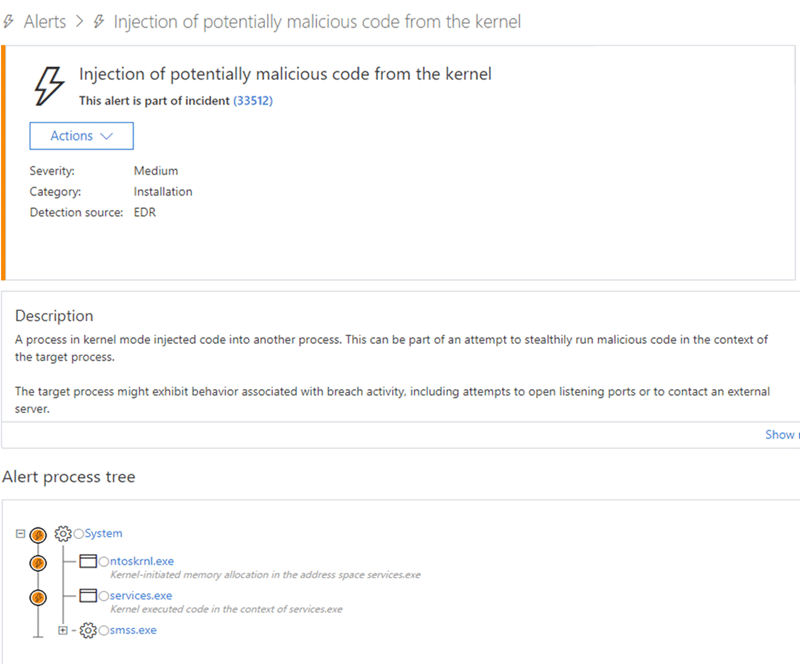
Microsoft found that PC Manager on Huawei allowed an attacker to create a new instance of MateBookService.exe and gain many administrator privileges. Huawei’s driver allowed a basic code to gain read/write permission and even modify the kernel as well. This lead to making a system vulnerable to complete compromise. The first instance was having a CVE-2019 score of 5241 while the other instance is of 5242.
However, the company has reported the flaw to Huawei, who responded quickly and cooperated very well in investigation and fixation of the issue. Microsoft reverse-engineered the driver and both the tech giants have successfully patched the privilege escalation flaw.