In the world of cybercrime, phishing ranks among the top crimes. Ignorant users get tricked into visiting malicious websites which may appear like the real one, share their sensitive information and maybe download malware into systems. One way to be protected from phishing attacks is to be cautious about which link you click.
One can never be sure of where an innocent-looking link could lead you. Granted, it is unrealistic to stop clicking links in general. So one option is to inspect all links you come across. Especially those coming from so-called friends or from sources which appear trustworthy.
Also, read: Password Secrets: Why Your Password is Never Secure
Contents
1. Checking for authenticity
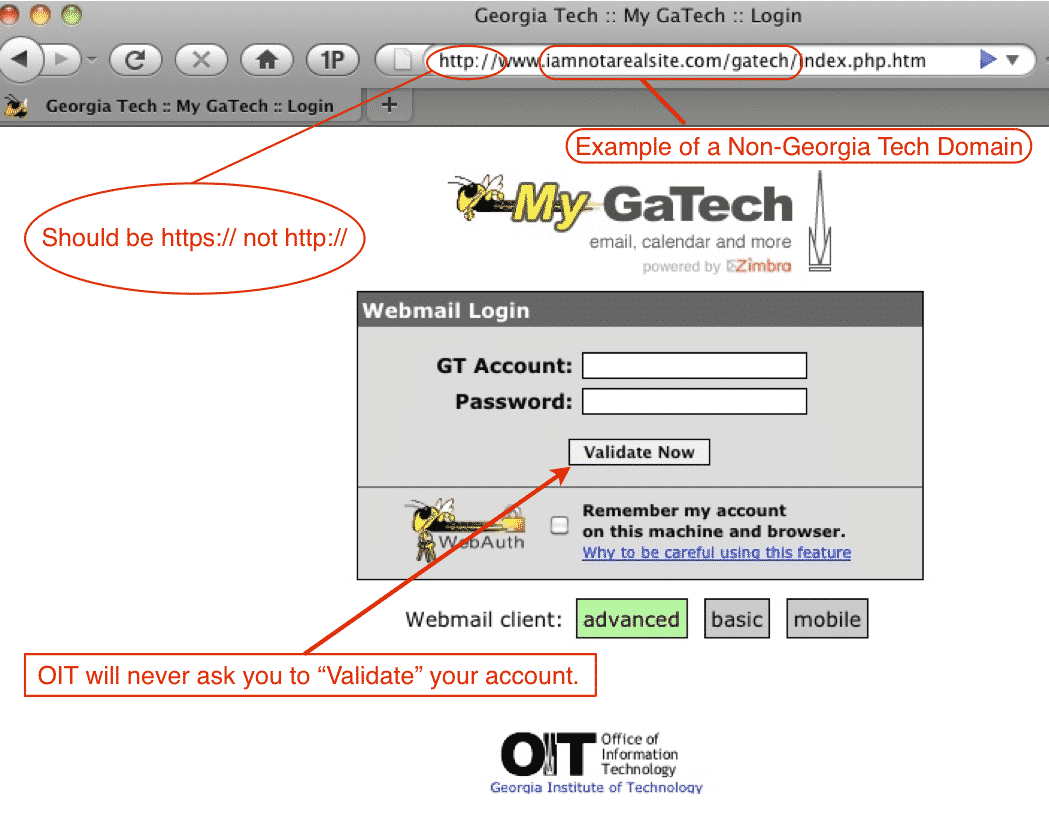
You receive an email supposedly from your bank, asking you to visit the website and log in to your account for a certain purpose. A link is provided at the bottom the page. Do not click it. The first thing to do is the copy said link and paste into your browser. Then examine it to ensure it matches the email of the company it claims to be.
Attackers are smart and will try to make the site’s URL look similar to that of the original site. You may see something like faceebook.com. Notice the double “e”? It appears similar to the original site: www.facebook.com. Watch out for such similarities. Double-check if you have to.
2. Checking for security
Always try to use sites with HTTPS (HTTP Secure). It is an extension of the Hypertext Transfer Protocol which was brought up to bring about more security over the internet. It especially prevents man-in-the-middle attacks and leads to more security over transactions which may or may not be sensitive in nature.
Even if a network is insecure, HTTPS will create a secure channel to and from it. Using (HSTS) HTTP Strict Transport Security will reduce vulnerability to SSL stripping attacks. Of course, a site with HTTPS doesn’t automatically make it safe on all grounds, but it should at least improve confidence. Other checks can be performed.
3. Inspecting shortened links
Some URLs are often shortened to track clicks, make it more pleasing to the eye. URL shortening also disguises the actual address. Actual legitimate companies may do this, but hackers could also exploit this to hide where a certain link could lead you. Shortened URLs can be inspected using an online tool at http://checkshorturl.com/. Simply paste the link into the blank and watch as the underlying site gets revealed. Now you know the actual address. It’s your choice to decide whether or not the site is worth visiting.
4. Using POST not GET for sensitive information
Anyone familiar with PHP may have heard of the POST and GET superglobals. They are both request methods used with HTTP. Conventionally, they are mostly used when uploading files and forms; log in and sign up forms included, our main point of interest. It is the developer’s job to make sure the right request is used.
It is widely accepted that the POST request should be used when submitting sensitive information like usernames, passwords etc. The GET request shows the requested and submitted info/parameters in the URL. So if you submit details like a password, it appears in the URL. This is a simple GET request:
/test/demo.php?username=value1&password=value2
Hackers could intercept such data and make use of it. Web browser history and server logs will show the URL, so even HTTPS could only protect such data in transit. In addition, the GET command lengthens URL by the added information it shows. The POST method doesn’t show the parameter, hence making it the option of choice for submitting sensitive info. Developers should take note of this. If you’re a user, you may want to be more vigilant about what exactly displays in the URL once you hit the submit button.
Conclusion
Cybersecurity is and always will be a grave issue. Being online has its pros and cons. While using the internet, keep yourself vigilant. Be guarded and always willing to inspect everything you come across especially links. Not everything that appears safe is. There will always be malicious people out there looking for their next victim. Don’t be a victim.