Sony Pictures may not be in the position indolently while its corporate data is being spread all over the internet, following the shocking hack of its servers in late November.
According to a reports and rumors which say two anonymous sources that the company is using Amazon Web Services servers in Tokyo and Singapore to execute a DDoS (denial of service) attack on the servers’ contribution its corporate data. A DoS attack generally uses many servers to cloud another server with data, rendering it slow or completely not viable.
It’s hard-hitting to tell if Sony Pictures is really using such an attack, and the company would not confirm it yet. It’s probable, although: A similar tactic which was used in the Napster days, when entertainment groups hired professional companies to slow down downloads of popular copyrighted files, daunting people from trying to illegally obtain such files.
If this is true, it will definitely sound like a pretty anxious move by Sony. On the internet, once the rat is out of the bag, it’s very hard to control the spread of information as it was proven in the recent leak of celebrity nude photos in September.
Sony is dealing this attack at its best, while a lot of the torrent files leading to Sony data were removed from the respective torrent sites that held them. One of the latest files from the Sony hack only took a couple of minutes to download; the files were kept so handily.
Re/Code’s report claims that hackers are thwarting Sony’s attacks by using a different type of file for the newer leaks. But we’ve tried downloading using one of the older torrent files, and the result was the same — we had the data within minutes.
If Sony really is using counter steps against hackers that purloin its data, it’s not that shocking: It’s perhaps doing all it can to stop the leaking more. Unluckily for Sony, making a download process annoying for someone wanting to download a Metallica album is very diverse from trying to stop a hacker group or a rival from getting corporate data that’s (was) much out in the open to all.
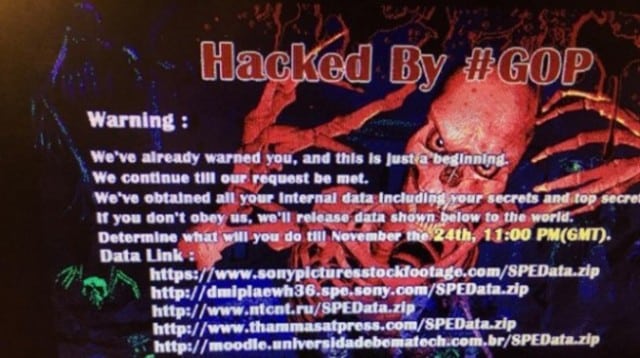
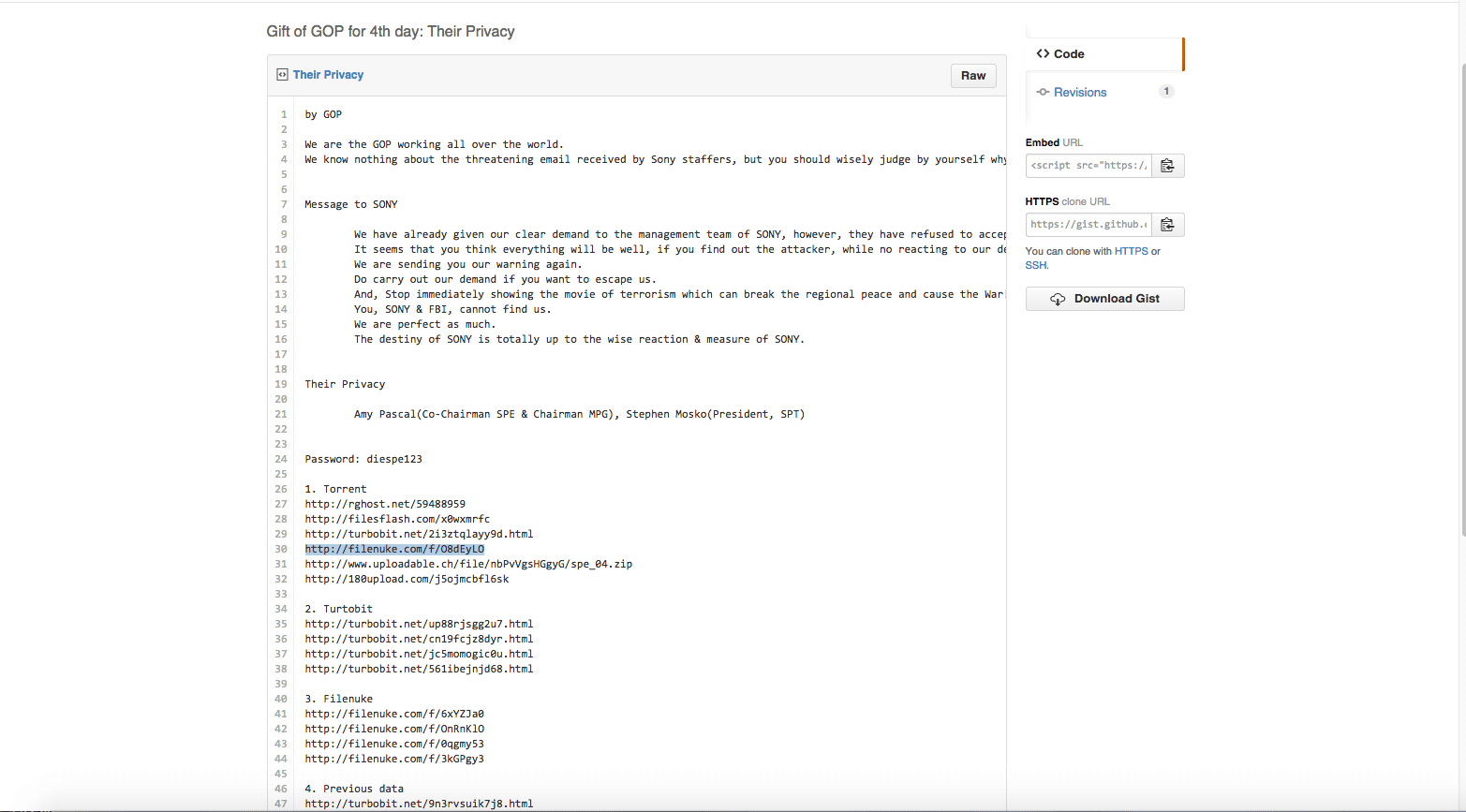
The Guardians of Peace, the hacker group that attacked Sony’s servers, has been time after time releasing new stuff of Sony’s corporate data in the last ten days. The data included Sony’s unreleased movies, financial info, scripts for and personal data of business execs and celebrities.
THE LATEST MESSAGE FROM THE ‘GUARDIANS OF PEACE’ HACKERS
We have already given our clear demand to the management team of SONY, however, they have refused to accept.
It seems that you think everything will be well, if you find out the attacker, while no reacting to our demand.
We are sending you our warning again.
Do carry out our demand if you want to escape us.
And, Stop immediately showing the movie of terrorism which can break the regional peace and cause the War!
You, SONY & FBI, cannot find us.
We are perfect as much.
The destiny of SONY is totally up to the wise reaction & measure of SONY.