The social and digital phenomenon has been perfecting itself as the internet progresses, and has been professionalized as all platforms increase their security. Your computer, email, and social media accounts must be using the best security approach available at this time but, are they really secure? There are always loopholes and vulnerabilities that make them easy to hack if you give an expert a try.
The same can be said for Wi-Fi security. You might have thought that using WPA2 Encryption for a Wi-Fi password will make it impossible to hack but that’s no longer true. A new flaw for Wi-Fi password hacking has been found that makes it easier for hackers to decipher the passwords of most routers. This attack was found accidentally while looking for new ways to attack the new WPA3 security standard.
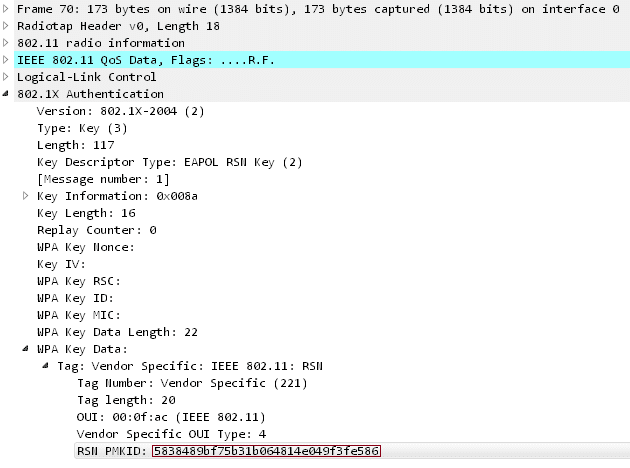
Jens Steube, the developer of “Hashcat” decryption tool, has discovered this new WiFi hack. It works explicitly against WPA/WPA2 Wi-Fi protocols with Pairwise Master Key Identifier (PMKID) based on roaming features. This innovative method allows attackers to get the Pre-shared Key (PSK) login passwords allowing them to even spy on Internet communications.
According to Jens, the previous WiFi hacking methods require attackers to wait for someone to log into a network and capture a full 4-way authentication handshake of EAPOL, which is a network port authentication protocol. But this new attack does not require a user to be on the target network to capture credentials meaning there is no need to capture a full EAPOL 4-way handshake. The new attack is made on the RSN IE (Robust Security Network Information Element) of a single EAPOL frame.
How to hack Wi-Fi password using PMKID?
1. You can use hcxdumptool (v4.2.0 or higher) to request the PMKID from the targeted access point and dump the received frame to a file.
$ ./hcxdumptool -o test.pcapng -i wlp39s0f3u4u5 –enable_status
2. Using the hcxpcaptool, the frame output can be converted into a hash format
$ ./hcxpcaptool -z test.16800 test.pcapng
3. Now you can use Hashcat (v4.2.0 or higher) tool to obtain the WPA PSK (Pre-Shared Key) password
$ ./hashcat -m 16800 test.16800 -a 3 -w 3 ‘?l?l?l?l?l?lt!’
This last step will give you the password of your targeted WIFI network but it may take some time depending on the length and complexity of the password.
At this time, we do not know for which vendors or for how many routers this technique will work, but we think it will work against all 802.11i/p/q/r networks with roaming functions enabled (most modern routers).
Steube said.
According to HashCat Forum the advantages of this technique are:
- No more regular users required
- No waiting for a complete 4-way handshake between the regular user and the AP
- Eventual retransmissions of EAPOL frames doesn’t happen (which can lead to uncrackable results)
- No more eventual invalid passwords sent by the regular user
- No more lost EAPOL frames when the regular user or the AP is too far away from the attacker
- No more special output format (pcap, hccapx, etc.) – final data will appear as regular hex encoded string
However, this new WiFi hack does not work against latest wireless security protocol WPA3, since the new protocol is “much harder to attack because of its modern key establishment protocol called “Simultaneous Authentication of Equals” (SAE).”
Since the new WiFi hack requires attackers to brute force the password, users are recommended to protect their WiFi network with a secure password that’s difficult to crack.





Just explain that those that make the software has also made ways so an administrator can reset routers. These “openings” are not a flawed design of the password, nobody has exposed a way to crack them, but found other ways so the routers respond with the password allowing an administrator to log-in and administer your details.
That this also can be used to guess password is an error. It should not be like this, it is a mistake.
The words “Error” and “Mistake” seems to be omitted on the net, and this is a gross mistake.
There are many tools like that from which we can hack wifi but they are not efficient in all type of protection and the method that i had mailed you . By that method you can hack any wifi on the earth that was very good content and you can’t get that content on any website even you will not get it on deep web and dark web , but i don’t know why you are not publishing it . No problem . your choice.
regards from
siddhant
Hye
Can you tell me anu tool for hacking wifi having wpa and wpa 2 security ?
Please mail that method to me…